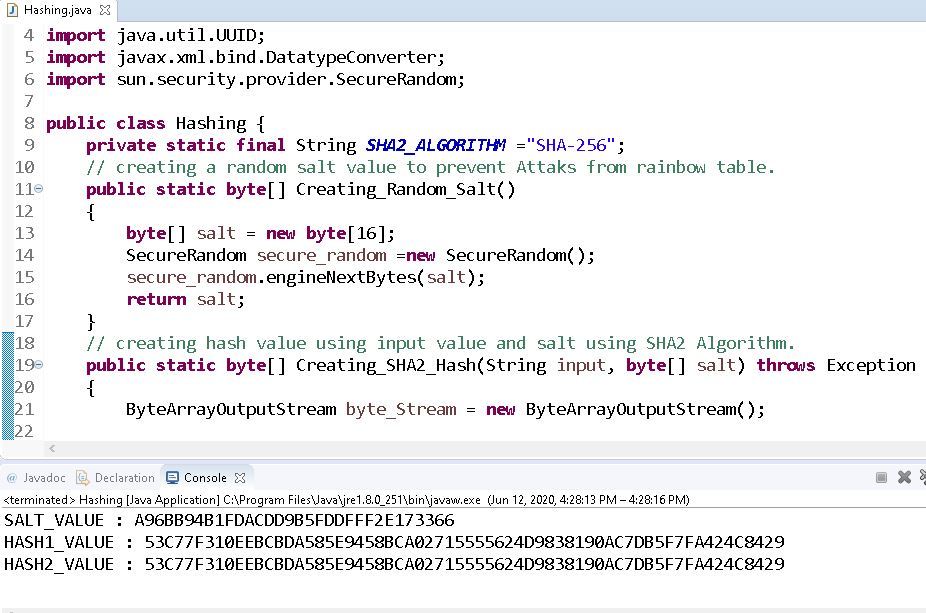
Hash Salt Example . A long randomly generated salt (using /dev/urandom) is expected to be globally unique. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Salt is combined with the password before hashing. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. Below is an example of a few words going through the hashing process. Thus salts can be used to make pre. However, salting a hash, in the. Password hashing is a key step to protecting your users on the backend, but it’s not. The password and salt clear values are concatenated and the resulting. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the.
from bingerconcepts.weebly.com
Password hashing is a key step to protecting your users on the backend, but it’s not. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. However, salting a hash, in the. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Thus salts can be used to make pre. Salt is combined with the password before hashing. Below is an example of a few words going through the hashing process. A long randomly generated salt (using /dev/urandom) is expected to be globally unique. The password and salt clear values are concatenated and the resulting.
Hash rate calculator bingerconcepts
Hash Salt Example Salt is combined with the password before hashing. Thus salts can be used to make pre. The password and salt clear values are concatenated and the resulting. A long randomly generated salt (using /dev/urandom) is expected to be globally unique. Salt is combined with the password before hashing. Below is an example of a few words going through the hashing process. However, salting a hash, in the. Password hashing is a key step to protecting your users on the backend, but it’s not. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the.
From thecyphere.com
Difference Between Encryption And Hashing Salt Cryptography Hash Salt Example Below is an example of a few words going through the hashing process. The password and salt clear values are concatenated and the resulting. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. Password hashing is a key step to protecting your users on the backend, but it’s not.. Hash Salt Example.
From www.exampleslab.com
20 Examples of Oxisales Salts Examples Lab Hash Salt Example You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Salt is combined with the password before hashing. However, salting a hash, in the. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. Password hashing is a key step. Hash Salt Example.
From www.howtoasp.net
The table with the passwordhash and salt values in Hash Salt Example The password and salt clear values are concatenated and the resulting. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. Salt is combined with the password before hashing. Below. Hash Salt Example.
From www.youtube.com
How to Salt & Hash a Password Using PHP and MySQL Create a Login Pt 3 Hash Salt Example Thus salts can be used to make pre. The password and salt clear values are concatenated and the resulting. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. Salt is combined with the password before hashing. Because cybercriminals use an array of resources in cyber attacks, a key step. Hash Salt Example.
From www.vaadata.com
How to securely store passwords in database Hash Salt Example A long randomly generated salt (using /dev/urandom) is expected to be globally unique. Salt is combined with the password before hashing. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. Password hashing is a key step to protecting your users on the backend, but it’s not. The password and. Hash Salt Example.
From bingerconcepts.weebly.com
Hash rate calculator bingerconcepts Hash Salt Example Below is an example of a few words going through the hashing process. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Thus salts can be used to make. Hash Salt Example.
From www.thesslstore.com
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed Hash Salt Example Password hashing is a key step to protecting your users on the backend, but it’s not. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; The password and salt clear values are concatenated and the resulting. Thus salts can be used to make pre. A long randomly generated salt. Hash Salt Example.
From ionbiosciences.com
PBFI K⁺ Salt Sodium Indicator ION Biosciences Hash Salt Example Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. The password and salt clear values are concatenated and the resulting. However, salting a hash, in the. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Thus salts can. Hash Salt Example.
From zhuanlan.zhihu.com
哈希算法在电子数据取证中的应用探讨 知乎 Hash Salt Example You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; The password and salt clear values are concatenated and the resulting. Salt is combined with the password before hashing. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. Because. Hash Salt Example.
From journal.swaledale.co.uk
Salt Beef Hash Recipe By Ryle Hash Salt Example A long randomly generated salt (using /dev/urandom) is expected to be globally unique. However, salting a hash, in the. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. Thus salts can be used to make pre. The password and salt clear values are concatenated and the resulting. Salt is. Hash Salt Example.
From www.ics.com
Ruin a Hacker's Day by Securing Your Application Layer ICS Hash Salt Example Thus salts can be used to make pre. However, salting a hash, in the. A long randomly generated salt (using /dev/urandom) is expected to be globally unique. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Below is an example of a few words going through the hashing process.. Hash Salt Example.
From www.youtube.com
Salted Password Scheme Applied Cryptography YouTube Hash Salt Example Salt is combined with the password before hashing. Thus salts can be used to make pre. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. A long randomly generated. Hash Salt Example.
From sciencenotes.org
What Is a Salt in Chemistry? Definition and Examples Hash Salt Example The password and salt clear values are concatenated and the resulting. Thus salts can be used to make pre. Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the. Password hashing is a key step to protecting your users on the backend, but it’s not. However, salting a hash, in. Hash Salt Example.
From www.blockchaines.tech
🥇¿Qué es el Hashing? Y aquello que Desconoces Blockchain es Hash Salt Example Password hashing is a key step to protecting your users on the backend, but it’s not. Below is an example of a few words going through the hashing process. However, salting a hash, in the. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and hashing. The password and salt clear. Hash Salt Example.
From www.cublockchainalliance.com
What is the hash in blockchain? UCBA Hash Salt Example You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; The password and salt clear values are concatenated and the resulting. A long randomly generated salt (using /dev/urandom) is expected to be globally unique. Password hashing is a key step to protecting your users on the backend, but it’s not.. Hash Salt Example.
From phpgurukul.com
How to Salt & Hash a Password using Sha256 , How to Salt & Hash a Hash Salt Example A long randomly generated salt (using /dev/urandom) is expected to be globally unique. Salt is combined with the password before hashing. Thus salts can be used to make pre. The password and salt clear values are concatenated and the resulting. Below is an example of a few words going through the hashing process. Password hashing is a key step to. Hash Salt Example.
From www.appspy.com
Hash & Salt password iPhone & iPad Game Reviews Hash Salt Example You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Below is an example of a few words going through the hashing process. Thus salts can be used to make pre. Because cybercriminals use an array of resources in cyber attacks, a key step in password security is salting and. Hash Salt Example.
From www.wordfence.com
Understanding Password Authentication & Password Cracking Hash Salt Example However, salting a hash, in the. Salt is combined with the password before hashing. You might wonder if you are reading a hash brown recipe as we are now talking about salting a hash; Password hashing is a key step to protecting your users on the backend, but it’s not. Salted password hashing can be used to improve password security. Hash Salt Example.